 Louisiana Commercial Realty is a top-rated commercial real estate company, instrumental in rebuilding New Orleans with some of the largest transactions ranging from office leasing to building new affordable apartments and developing French Quarter hotels, but we are a small boutique working mostly from referrals so when our website was hacked it was a real surprise hearing our webmaster say it could be Russians.
Louisiana Commercial Realty is a top-rated commercial real estate company, instrumental in rebuilding New Orleans with some of the largest transactions ranging from office leasing to building new affordable apartments and developing French Quarter hotels, but we are a small boutique working mostly from referrals so when our website was hacked it was a real surprise hearing our webmaster say it could be Russians.
The hacker got in, bypassed security with encrypted passwords, only to post half a dozen bad grammar articles with links to sell Viagra. It took a lot of work to hack past our website's guard, so you can only surmise that they must be hacking millions of sites to reach the one-half of one percent that actually click a strange link in a blog to make the hackers a few pennies from selling Viagra.
The hacker posted several articles, about a page in length, on topics about negotiation, which is a common blog subject since I was trained by the NASD in negotiating and happen to have a funny video on negotiating with a lighthouse on my website. The hacker's articles all came at once, all with the same poor syntax and run-on sentences, and all on the topic of negotiation. I even got one like on Facebook. I spent the last 2 months and several thousand dollars fixing my website, and here is how it can happen to you.

Websites start with a domain name, and you can buy them through just about any web hosting company. Mine was purchased for $12 through GoDaddy. You can buy any domain name, as long as someone hasn't beaten you to it which means it has already been registered in a central database. Domain name registration got its start when Jon Postel at University of Southern California had a contract with the United States Department of Defense. Then in 1998, the Internet Corporation For Names and Numbers (ICANN) was founded, to maintain the database of domain names and Internet Protocol addresses (your computer's equivalent of a social security number).

Securing your domain name simply guarantees nobody else can get it, but to have a website you need a web host: the company that has a computer server somewhere, usually in Oregon, Utah or Virginia, that stores the code with the information you have on your website. You can pay almost any company to host your website and they in turn will pay a data center to store your website information. I use GoDaddy to host 2 of my 3 websites. Without the hosting services, you won't have a place for your files to reside, so your domain would then become like a disconnected phone number in the phone directory, and your site files would have nowhere to stay. The web-hosting server knows how to read these files, which explain how the webpage looks or instruct the server to do a series of computations. These computations are things like figuring out what blog article it's supposed to send back to the viewer.

Webmasters usually have their name at the very bottom of their page, and sophisticated hackers can try thousands of iterations of the webmaster's name to obtain an email address, then send the webmaster an official looking mock form to change some administrative problem, but when the webmaster logs in to the host, the hacker can store the login info and have access to the host.
The hacker needs the host ID login and a password, and another method to obtain them is called a Brute Force Attack: when a hacker tries many combinations of usernames and passwords until they succeed in guessing the right combination. Due to the fact that at any one time there may be many concurrent login attempts occurring on your site via malicious automated robots, this also has a negative impact on your server's memory and performance. The correct settings in your host admin section will stop the majority of Brute Force Login Attacks at the .htaccess level thus providing even better protection for your login page and also reducing the load on your server because the system does not have to run PHP code to process the login attempts. The only way to prevent this is to set your host admin rules to block any attempt to log in after one failed attempt.
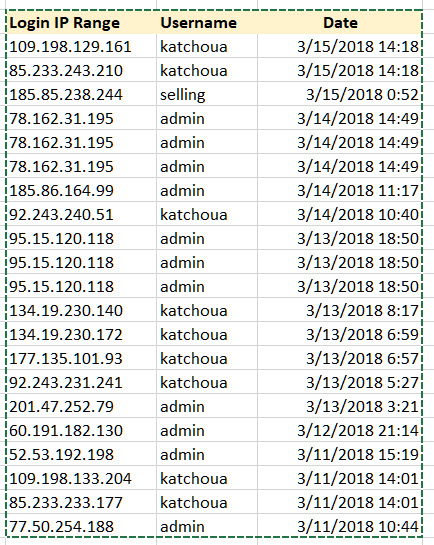
 Hacker's use thousands of different IP addresses to not only bypass a lockdown caused by a failed login attempt, but also to make it difficult to track them down and prosecute. My host has a security screen that tracks failed login attempts IP addresses, and the results show my hacker tried over 1,000 times to access my website over a 3 month period, but here is a sample of jut 4 days of hacking activity showing each time the hacker tried a different username and was locked out when the password didn't match. Tracking down the IP addresses has proven impossible, but you can tell most hacking is done from midnight to 4am...definitely not a baby boomer:
Hacker's use thousands of different IP addresses to not only bypass a lockdown caused by a failed login attempt, but also to make it difficult to track them down and prosecute. My host has a security screen that tracks failed login attempts IP addresses, and the results show my hacker tried over 1,000 times to access my website over a 3 month period, but here is a sample of jut 4 days of hacking activity showing each time the hacker tried a different username and was locked out when the password didn't match. Tracking down the IP addresses has proven impossible, but you can tell most hacking is done from midnight to 4am...definitely not a baby boomer:
For more than 150 articles on commercial real estate, read our blog at website www.louisianacommercialrealty.com.
For current prices on all types of commercial property, including retail, industrial, office, check out our charts page .